The article "Maximizing Measurement Precision with Strategic Sensor Placement" emphasizes the significance of strategically situating sensors to optimize measurement precision in engineering and scientific applications. It highlights the importance of considering environmental characteristics and system dynamics to identify informative sensor locations. Furthermore, it discusses the use of advanced algorithms, modeling techniques, and smart sensor placement strategies to continuously optimize measurement processes and enhance accuracy. Similarly, the article "Enhancing Accuracy through Intelligent Sensor Positioning" underscores the pivotal role of smart sensor placement strategies in optimizing data collection. It emphasizes leveraging advanced algorithms, predictive modeling, and machine learning to ensure precise data acquisition and dynamic refinement of sensor positioning. Both articles provide comprehensive insights into the multifaceted task of maximizing measurement precision and enhancing accuracy through intelligent sensor placement, making them essential reads for engineers and scientists seeking to improve the effectiveness of sensor networks.

The article "Essential Techniques for Mastering Technical Climbing Routes" discusses crucial techniques for success in tackling complex climbing routes, emphasizing the importance of precision footwork, body positioning, finger strength, and route interpretation. The essential skills and mental focus necessary for conquering technical climbs are highlighted, with an emphasis on the need for deliberate practice and training to improve capabilities and confidence. Moreover, the piece "Overcoming Challenges: Strategies for Success on Technical Routes" underscores the importance of analyzing routes, honing technical skills, and developing mental resilience to navigate the challenges of technical climbing effectively. Overall, both articles advocate a multifaceted approach to mastering technical routes and offer valuable insights for climbers seeking to enhance their climbing abilities and conquer challenging routes.

In today's competitive business environment, the pivotal role of data analysis in enhancing business strategy cannot be overstated. By leveraging data analysis, businesses gain crucial insights into emerging trends, customer preferences, and market opportunities, essential for crafting adaptive business strategies. Moreover, effective data analysis allows businesses to tailor products and services, optimize resource allocation, and make data-driven adjustments to their overall business strategy. Harnessing the power of advanced analytics tools and technologies enables businesses to anticipate market shifts, capitalize on emerging opportunities, and mitigate potential risks, driving informed decision-making. The strategic importance of leveraging data analysis for informed decision-making cannot be overlooked, as it provides actionable insights and empowers businesses to navigate through complex and competitive landscapes.

The article discusses the significance of covert observation in surveillance and investigative practices, emphasizing its role in gathering discreet, accurate, and timely information without alerting the subjects under scrutiny. It highlights the value of this clandestine method in uncovering illicit activities, gathering incriminating evidence, and providing real-time insights into the behavior and movements of suspects. The author also underscores the ethical considerations and limitations associated with covert observation, stressing the need to navigate privacy concerns and biases while acknowledging the partial view it provides. Overall, the article presents a compelling case for the importance of covert observation in investigative work, while also highlighting the need to approach it responsibly and ethically, making it a must-read for those involved in surveillance and investigative practices.
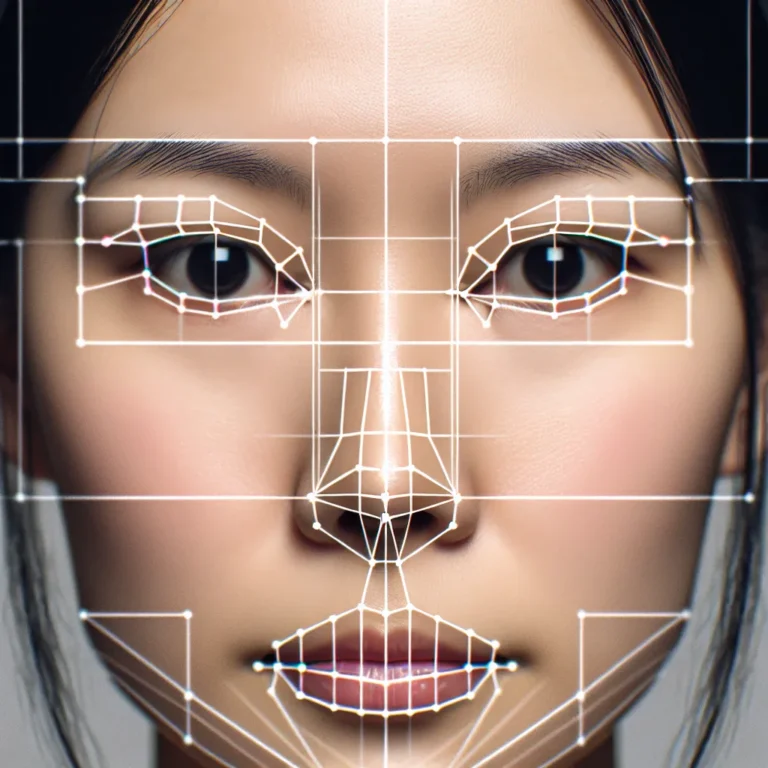
The article explores the issues and limitations of facial detection systems, highlighting concerns regarding biases, inaccuracies, environmental factors, and privacy breaches. It emphasizes the ethical implications and societal inequalities associated with these systems, calling for stringent regulations and improved frameworks for responsible and equitable use. Additionally, it discusses the challenges in facial recognition technology, focusing on accuracy, privacy, and demographic bias. The article suggests that advancements in algorithms, data security measures, and efforts to address biases are crucial in overcoming these challenges and ensuring the widespread adoption of facial recognition technology. If you're interested in understanding the complexities and potential solutions in the field of facial detection and recognition, the full article provides valuable insights in addressing these critical issues.

The integration of artificial intelligence (AI) has revolutionized surveillance technologies, enabling enhanced threat detection capabilities through sophisticated analysis of large data volumes in real-time and the development of advanced facial recognition and behavior analysis systems. However, concerns about the ethical implications of AI-driven surveillance on civil liberties and privacy rights have been raised, necessitating robust regulatory frameworks for responsible and ethical use. Similarly, the implementation of biometric surveillance systems has raised significant ethical considerations regarding privacy, consent, and potential misuse of personal data, as well as debates about government or corporate control over individuals' movements and the necessity of informed consent. While these technologies offer undeniable benefits in enhancing security and efficiency, addressing the ethical considerations is crucial to ensure the respect of individual rights and uphold fundamental ethical principles.

The article "The Evolution of Covert Operations: From Espionage to Cyber Warfare" explores the shifting landscape of warfare, delving into the transformation of covert operations from traditional espionage to the realm of cyber warfare. It highlights the significant impact of technological advancements in reshaping the nature of covert activities, providing a global reach for clandestine operations with an unprecedented level of anonymity and deniability. The rise of cyber warfare has redefined the scope of covert operations, emphasizing the importance of technological expertise and the complexities of navigating the digital domain. Moreover, it reflects the increasing interconnectedness of the modern world, laying the groundwork for the prominent role of cyber warfare in shaping the future of modern warfare. On the other hand, the article "The Impact of Covert Operations on Geopolitical Dynamics" underscores the profound influence of covert operations on geopolitical dynamics, detailing how these clandestine activities conducted by state actors can destabilize regions, erode trust between nations, and trigger international crises. It emphasizes the intricate interplay between covert activities and the geopolitical landscape, highlighting the multifaceted consequences that extend beyond immediate tactical goals and their crucial significance in understanding global politics and security dynamics. This comprehensive analysis provides a compelling glimpse into the intricate and impactful realm of covert operations, inviting readers to explore the full breadth of the articles for a deeper understanding of these complex phenomena.

The article "Route Analysis Methods for Traffic Optimization" delves into the crucial role of route analysis in managing transportation networks. It highlights the use of historical traffic data, Geographic Information System (GIS) tools, simulation techniques, and advanced technologies like machine learning and artificial intelligence to optimize travel times, predict traffic volumes, and alleviate congestion points. The article stresses that by leveraging these methods, traffic engineers can continuously improve route efficiency and enhance transportation systems, ultimately leading to a more efficient and responsive travel experience for commuters. Additionally, the companion piece "Techniques for Effective Route Planning" emphasizes the importance of effective route planning in minimizing travel time and reducing traffic congestion, especially in urban areas. The article discusses the utilization of real-time traffic data analysis, predictive modeling, and smart technologies to optimize routes and improve traffic flow. It encourages readers to explore the advanced techniques outlined to gain insights into traffic optimization strategies and their potential impact on overall transportation system enhancements.







