
The article explores the historical relationship between technology and covert operations, highlighting how advancements in technology have continuously reshaped the landscape of espionage and intelligence gathering. It delves into the pivotal role of technologies such as telegraph, radio communication, encryption, and decryption methods during the early 20th century and the surge of innovation during the Cold War, leading to the birth of spy satellites and surveillance capabilities. Additionally, it discusses the impact of the internet age and the current influence of artificial intelligence, facial recognition, and cyber warfare technologies on covert operations. The integration of cutting-edge technologies and their potential to shape the future of covert operations is emphasized. The article provides a comprehensive overview of how technology has influenced and continues to transform the world of intelligence agencies, making it an intriguing read for those interested in the intersection of technology and covert operations.

The article "The Evolution of Covert Operations" traces the development of covert operations from ancient espionage to modern cyber warfare and misinformation campaigns. It highlights the significant transformations in the world of covert operations, emphasizing the impact of geopolitical changes and technological advancements. The article also explores the role of intelligence agencies in gathering and analyzing information to address global security challenges, emphasizing the importance of international cooperation and providing valuable insights to policymakers. It concludes by emphasizing the dynamic and ever-evolving nature of covert operations in response to technological, geopolitical, and warfare developments. This comprehensive overview serves as an insightful introduction to the intricate world of covert operations, offering a compelling read for those interested in understanding its historical context, contemporary relevance, and future implications.

The article discusses the pressing concerns surrounding personal privacy in the digital age, with the proliferation of surveillance technology such as CCTV cameras, facial recognition, and data tracking software. It addresses the ethical and legal implications of constant monitoring and data collection, emphasizing the potential for unwarranted intrusion into private lives. Furthermore, it highlights the pervasive impact of surveillance technology on personal privacy through the extensive collection and analysis of personal data, raising concerns about the protection of individual privacy in the digital landscape. The article concludes by emphasizing the need for proactive measures to address the ethical, legal, and technological dimensions of this complex issue in order to safeguard personal privacy. Additionally, it provides strategies for protecting privacy in a digital world, including encryption, conscious management of personal data, the use of virtual private networks (VPNs), and staying informed about privacy laws and regulations.
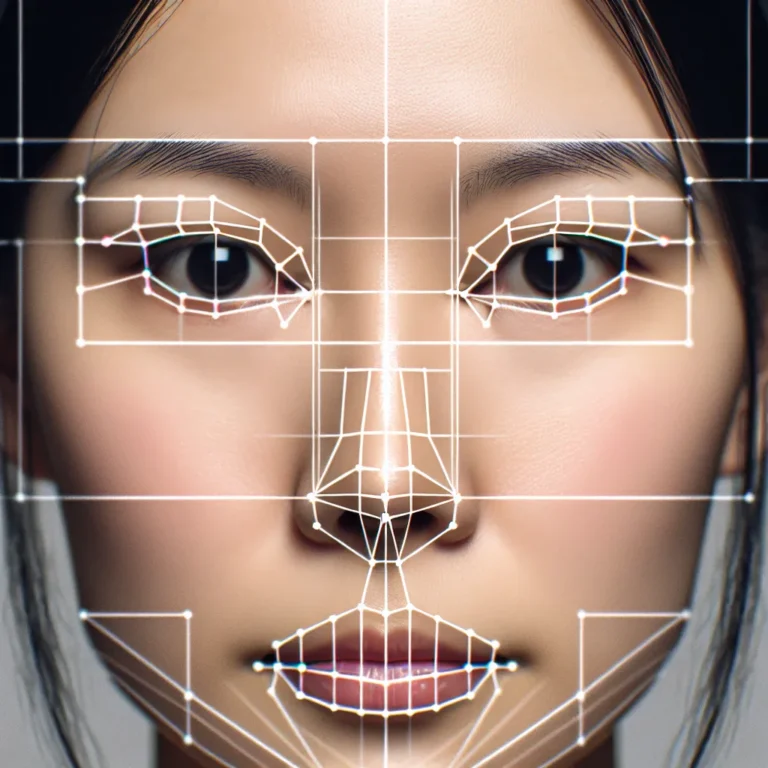
The article explores the issues and limitations of facial detection systems, highlighting concerns regarding biases, inaccuracies, environmental factors, and privacy breaches. It emphasizes the ethical implications and societal inequalities associated with these systems, calling for stringent regulations and improved frameworks for responsible and equitable use. Additionally, it discusses the challenges in facial recognition technology, focusing on accuracy, privacy, and demographic bias. The article suggests that advancements in algorithms, data security measures, and efforts to address biases are crucial in overcoming these challenges and ensuring the widespread adoption of facial recognition technology. If you're interested in understanding the complexities and potential solutions in the field of facial detection and recognition, the full article provides valuable insights in addressing these critical issues.

The article "The Evolution of Covert Operations: From Espionage to Cyber Warfare" explores the shifting landscape of warfare, delving into the transformation of covert operations from traditional espionage to the realm of cyber warfare. It highlights the significant impact of technological advancements in reshaping the nature of covert activities, providing a global reach for clandestine operations with an unprecedented level of anonymity and deniability. The rise of cyber warfare has redefined the scope of covert operations, emphasizing the importance of technological expertise and the complexities of navigating the digital domain. Moreover, it reflects the increasing interconnectedness of the modern world, laying the groundwork for the prominent role of cyber warfare in shaping the future of modern warfare. On the other hand, the article "The Impact of Covert Operations on Geopolitical Dynamics" underscores the profound influence of covert operations on geopolitical dynamics, detailing how these clandestine activities conducted by state actors can destabilize regions, erode trust between nations, and trigger international crises. It emphasizes the intricate interplay between covert activities and the geopolitical landscape, highlighting the multifaceted consequences that extend beyond immediate tactical goals and their crucial significance in understanding global politics and security dynamics. This comprehensive analysis provides a compelling glimpse into the intricate and impactful realm of covert operations, inviting readers to explore the full breadth of the articles for a deeper understanding of these complex phenomena.





